(Note: This message was originally intended for our own employees, but we decided to post it publicly, since it could benefit any of our customers or partners who might be targeted by similar attempts.)
Phishing scams are no joke, and in recent months we’ve seen a huge influx of scam messages purporting to be from Microsoft, Google, or other commonly used office software providers. Fortunately, there are two easy rules that, if you follow them, can help you spot nearly 100% of scams before you click on them.
- Completely ignore what the email looks like. That includes any images, company names, and logos – as well as what the text says.
- Find out where the links in the email lead. If the URL doesn’t match the address of the company it purports to be from, it is unquestionably a phishing scam.
In the simplest sense, that’s all there is to it. But let’s take a moment to explain why it works – and the really crucial part, which is how to identify the real URLs behind a fake email’s links.
Completely ignore what the email looks like
This may sound counterintuitive at first, but it’s important to understand that when you receive a scam email, literally everything that you can see is designed to trick you. The design is intended to fool you into thinking it came from a legitimate company, and the words in the text are designed to trick you into taking action. Neither one gives you any information about who actually sent the message.
 Duplicating an official company sign-in page is as simple as saving the pictures and colors, then using them to make your own copy. Duplicating an official company sign-in page is as simple as saving the pictures and colors, then using them to make your own copy. |
Remember that it is very, VERY easy for a scammer to make an email or web page look like whatever he wants. And copying companies’ “official” sign-in pages or email templates is no exception.
Any competent web designer can go to a company’s real sign-in page, grab the images, colors, fonts, and create an identical fake page in a matter of minutes. The same goes for email templates. So, the mere fact that a message contains the real company’s name and logo means nothing.
Similarly, the scammer can make the text say whatever he wants, and it is usually something along the lines of: “There is an urgent problem with your account and you need to click here to solve it.” There is nothing that helps you identify who the message is from.
It should be noted that, while the look and content of the email can almost never tell you whether it’s real, there are two cases where it can help you tell that it’s a scam.
The first is the “from” email address. Any scammer worth his salt will “spoof” this address – in other words, he’ll fake the “from” part of the email to make it looks like it came from the company he’s pretending to be.
An example of an email in which the sender has faked the name to make it appear like it’s coming from a legitimate company. |
But, depending on the scammer’s sophistication, he might have managed to fake only the company’s name, or both the name and the email address. So, if you see a mismatch between the two, as in the example here, you can be sure it’s a phishing attempt.
However, you can’t rule out a scam if the name and email address appear to match. A good scammer can fake the email domain too, or at least use a very similar domain that can fool you if you’re not careful. More on this later.
The second case where the content of a message can identify a scam is when there is a text link that leads somewhere other than what the text says. This is essentially the same thing that we will be talking about in the next section, though, so we will cover it there.
Find out where the links really lead
If you learn nothing else about phishing emails from this article, this is the one thing you should take away. Once you learn how to do it, you’ll never fall for a scam again. All you need to know is how to tell the “real” destination of a link or image that you are about to click on. We’re about to tell you how to do that.
Remember how we said never to trust what the text and images in an email look like? The same thing goes for links. Just as it’s very easy to make a web page or email template look like whatever you want, you can make a link say whatever you want as well. In particular, it’s very easy to make the text say one thing but the link point somewhere else. For example:
Sign In to Microsoft Outlook Sign In to Microsoft Outlook
The two links above look exactly the same, but the one on the left leads to the legitimate Microsoft Outlook site, while the one on the right leads somewhere completely different (in this case, our own site, www.digitalcheck.com). This goes to show that the text on the screen has nothing to do with where the link leads. That’s contained in the code behind the page, which you can’t see by default. To illustrate this, the following code …
<a href=”https://www.digitalcheck.com”>Google</a>
… will produce the following link …
… which leads to www.digitalcheck.com.
If it’s a phishing email, the visible text will just be part of the scam – it’s there to fool you. So ignore it and find the real target of the link.
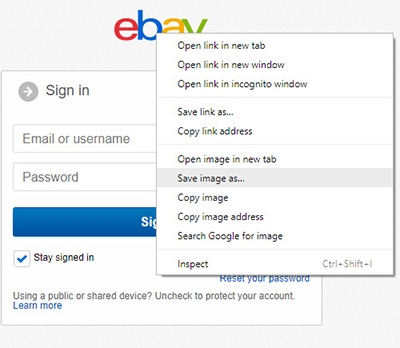
 Hovering over – but not clicking – an image or text link will reveal its actual destination. |
How do you do that? The simplest way is to hover your mouse over the link (or button) without clicking it. This works for both text links and images, and will reveal the link as shown at right.
In many email programs, you can also right-click the link, select “Copy Hyperlink” (Outlook), “Copy Link Location” (Firefox), “Copy Link” (Edge), or “Copy Link Address” (Chrome), and then paste that somewhere else that lets you see the text. This is how you find the REAL destination of the link.
Now, what do you do with that information? The next step is being able to tell a legitimate destination URL from a fake one, and there is one easy rule for doing that:
Only pay attention to the last two places in the destination address. We call this the “Second-to-Last-Dot Rule” or the “First Slash Rule.”
What that means is, ignore anything that comes before the second-to-last dot in the URL. Also ignore whatever comes after the first slash in the address. That would mean, ignore everything except:
- the “microsoft” and “.com” in https://www.microsoft.com/
- the “amazon” and “.ca” in https://www.amazon.ca/ap/signin?_encoding=UTF8
- the “scam” and “.co” in https://login.office.microsoft.com.scam.co/microsoft-outlook-login/
Notice a pattern? In each case, the REAL address behind the link is what comes right after the second-to-last dot (in red) and before the first slash (in green) of the address, also known as the “root domain name” or simply the “domain name.”
Why is this important? Because the root domain name – what comes after the second-to-last dot but before the first slash – is the only part of a website’s address that scammers can’t change. You need to own the domain.
For example, if you own the domain digitalcheck.com, you can put whatever you want before the “digitalcheck.com,” including any number of dots, and you can also put anything you want after it. Let’s say you were trying to steal Amazon passwords. You could create any of the following URLs and set up a fake sign-in page hosted there:
- www.digitalcheck.com/
- amazon.digitalcheck.com/
- amazon.customer.login.digitalcheck.com/
- www.digitalcheck.com/amazon/
- www.digitalcheck.com/login/amazon-customer-service/
- amazon.us1.digitalcheck.com/customer-login/
- us1.amazon-login.digitalcheck.com/amazon/login/my-account/
But in order to receive any of the incoming clicks in the examples above, you’d have to own the domain name digitalcheck.com and have your fake page set up there. (If you didn’t own the domain, you wouldn’t be scamming anyone; you’d just be sending them to the Digital Check website.)
So, the “real” site is revealed by what comes between the second-to-last dot and the first slash. Scammers can’t fake this part, so it is the one thing that will always be a dead giveaway.
Instead, they’re left with trying to disguise their own scam site as a legitimate one by adding stuff before and after the root domain, and hoping it’s good enough to fool you. Remember, it’s only what comes after the second-to-last dot that counts – the URL https://microsoft.login.com.x.co doesn’t go to microsoft.com or microsoft.login.com – it goes to x.co.
 Scammers will often register fake domain names that are similar to the one owned by a legitimate company. Using hyphens to mimic the URL, as in this example, is a common tactic. |
Some of these fakes can still be quite good – for example, this one in which the scammers registered the domain name “one-note.com.” Despite having a different base URL from the legitimate “onenote.com,” they might be able to pass it off for the real thing if the user isn’t paying close attention.
Legitimate companies will rarely use a hyphenated domain for a “main” company website – so as a rule, if you notice a hyphen after the second-to-last dot, be suspicious. If you have any doubt as to the authenticity of a URL, the best course of action is to do a separate search for the real site and see if the URL matches.
Remember, it’s not difficult to set up a fake URL, either – anyone can register an unused domain name for a few dollars in a matter of minutes. So merely having a website address that looks like a real company’s name is no guarantee at all. Do a search to make sure it’s the real thing.
It’s worth noting that the same general principles also apply to email addresses – in the example we used earlier, the message had an apparent title of “Office 365 Team,” but was really coming from the URL “ominio365.com.” Still, it’s the links you need to worry about more than the email address; just keep this in mind as a possible tip-off. If you have any doubts about the origin of the email, you can always just click the “reply” button and see what auto-populates in the “To” field. (Obviously, don’t actually send the message.)
To summarize our tips for avoiding phishing scams:
- When trying to figure out if the message is a scam, ignore the images, design, and text – they can all be manipulated to trick you. Focus on the source of the email and the URLs of the links.
- If the “from” email address has a URL different from the legitimate company’s, delete the message.
- If you think the sender’s identity may be masked, hit the Reply button in Outlook, and see what auto-populates as the actual return address. If it doesn’t match the source, delete the message.
- Hovering your mouse over a link (without clicking!) will display the “real” destination URL. Again, if it doesn’t match the legitimate company’s website address, it’s a scam.
- Only the root domain – the part after the second-to-last dot but before the first slash – in a URL is what matters. Everything else can be faked.
- If the URL in a link contains any hyphens, be suspicious.
- If the message itself contains any misspellings or grammatical errors, be suspicious.
- Above all, if you were not expecting the message, treat it with extra caution!
We hope this has been a useful read for you. If it helps even one person avoid a phishing scam, it’s worth it!